How to establish a behavioural baseline
Managing a successful security programme to tackle the issue of poor security behaviour is a significant challenge, even for the most mature organisations. Typically an organisation is given a small budget and the security team is set unrealistic expectations to reduce the impact of human behaviour on security; management typically expect this team to primarily meet a regulatory requirement, with no other tangible benefits. The danger here is that organisations design an ‘awareness programme’ with the end goal in mind, rather understanding the key problems first and addressing them this way instead…
As identified in the first blog behaviour is complex and can be influenced by a number of disruptive factors. Addressing the impact these factors are having on the behaviours of the workforce is paramount when ‘establishing a behaviour baseline’ – e.g. taking meaningful steps to understand the current behavioural profile of the organisation should enable the organisation to focus their future investments more effectively.
Establishing a behaviour baseline:
Many organisations invest in a ‘solution’ without understanding the problem. They miss the critical step of measurement and setting a benchmark before investing in a programme, then they fail to understand why they cannot demonstrate a return on investment or the impact the programme is having on behaviour. For example, they buy an out-of-the-box phishing simulation or force employees to conduct blank security awareness training. From the outset, it is highly unlikely that these solutions are suitably targeted enough to impact the security behaviour of the workforce at scale.
To set the organisation up for continued success they need to first establish the degree of influence each of the six behavioural factors is having on the behaviour of the workforce (e.g. across the entire organisation, by department, or even by role). By using the below spider diagram, we can effectively visualise information to guide future investment:
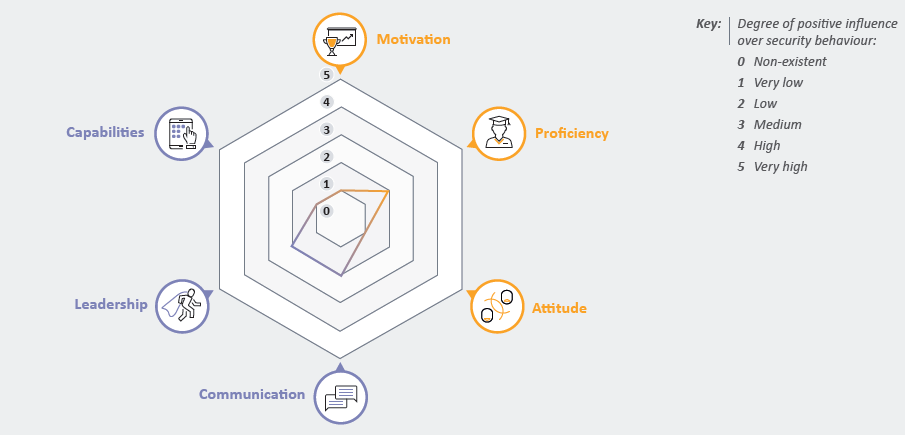
We can collect evidence of the current security behaviour of the workforce and map it to this diagram in two ways: quantitatively and qualitatively. For example, we can gather historic data sets about key risks and threats associated with behaviour from incident and audit logs, risk assessments and live data sets from data leakage prevention, or user and entity behaviour analytics. On the other hand, we can understand patterns of behaviour by observing the workforce, running cybersecurity exercises and testing behavioural responses. At the end of this step, we can gather far more detailed insights about the reasons behind behaviour, rather than expecting training and education to be the solution to all behaviour-related problems.
For example, this key step may in fact highlight that the organisation has a leadership problem, where senior management fail to set good behaviour examples for the rest of the workforce; or it may indicate that the workforce do not have the right security tools and systems in place to minimise and mitigate risks or report potential incidents. There is a wide spectrum of potential reasons behind behaviour, so narrowing this down is key when planning and investing in the right initiatives.
The findings at this key step must also be saved to demonstrate the impact the initiatives have had on the behaviour of the workforce at the end of the programme. A visual demonstration of the impact these initiatives have had on these six behavioural factors is an excellent communication tool for senior leaders to ensure future investment and attention.
