Threat Horizon 2022: Neglected infrastructure cripples operations

In a world where constant connectivity and real-time data processing is vital to doing business, even brief periods of downtime will have severe consequences. With the rise of decentralised data processing capabilities, organisations that do not adequately secure both their physical and digital estate will leave themselves vulnerable to severe disruption.
Threat 2.1 Edge computing pushes security to the brink
As the world sees the continued growth of the Internet of Things (IoT) and faster network speeds, this will give rise to far smarter and increasingly connected environments. The requirement for near-instantaneous connectivity and reduced latency will invigorate to edge computing technologies, architectures and solutions. The desire for edge computing could see its market value grow to $28 billion by 2027.
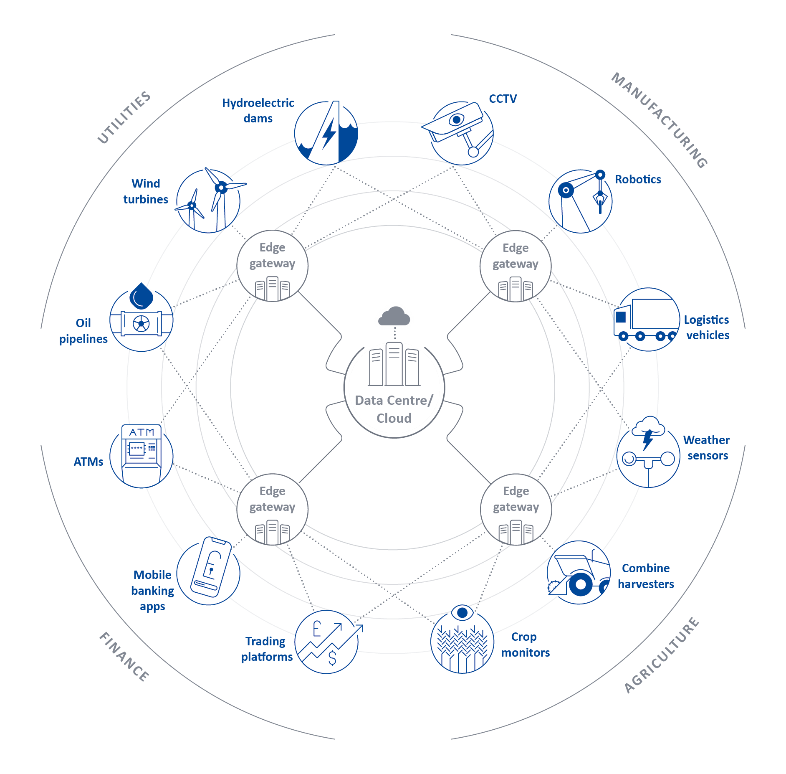
Whilst for many organisations the move to cloud service providers is now becoming established practice, by design it lacks many benefits that organisations and consumers will require in the coming years. Cloud services present issues surrounding latency as there is a significant lag between where data is created and where it is processed (in the cloud environment). Edge computing will allow organisations to process data and information by devices at the periphery or ‘edge’ of a specific network environment, significantly reducing that latency.
This key capability of edge computing will enable organisations to adapt to the environment in real-time; devices will now be able to make micro-adjustments and calibrations based on sensor inputs and the specific localised requirements of the user.
However, like with all technologies edge computing will introduce an array of new and existing challenges and threats. As edge computing increases both the number of physical devices and adds a web of ‘mesh networks’ in a much larger network environment, it extends organisational risk by further increasing the attack surface and providing greater opportunity for attackers to exploit security blind spots.
Utilities Sector:
One of the largest areas of uptake in edge computing has and will continue to be the utility sector, specifically in the case of renewable energies such as wind power. Edge computing allows the processing of data to take place at the source. Turbines combined with edge computing technology will be able to adapt to changing weather conditions in real-time changing the energy outputs required by the motor and adjusting the position of the blades to maximise performance.
- Attackers will seek to capitalise on the lack of security oversight that organisation will have on these monolithic architectures and infrastructures by taking advantage of poor physical security around edge devices. These attacks will create chaos as they have the potential to result in large scale blackouts of specific geographical locations or targeted populations. It is then no surprise that a report by Kollective in 2019 revealed that 66% of respondents considered edge computing to pose a growing threat to their organisations in the future.
