Security Think-Tank: Tackle insider threats to achieve data-centric security
The belief that effective perimeter security is the best way to protect data is a fallacy that is being repeatedly exposed. We must recognise the need for a data-centric security model to protect data from both internal and external threats, but what does this mean for security professionals?
Perimeter-centric controls are vital for stopping adversarial (and sometimes also accidental) threat actors. However, they have little to no effect against insiders and become all but useless once a breach occurs.
To optimise security arrangements, organisations should adopt a data-centric security model that makes use of preventative, detective and reactive controls, putting in place measures that assume breaches will happen so as to create organisational resilience.
Insiders are involved in the majority of security incidents. This can be with malicious intent (such as stealing data from the organisation), by accident (misconfiguring a system, for example) or through negligence or inadvertent error (such as falling victim to phishing – the most common vulnerability).
As insiders are able to bypass many controls, perimeter-based solutions are not adequate to protect an organisation. Additional measures are required for each stage of the information lifecycle to ensure data is protected as it is copied, shared, reused, repurposed, backed up or archived.
Variations of the information lifecycle exist. The ISF uses the following information lifecycle: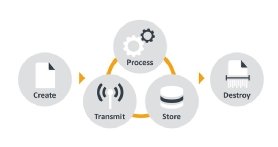
Throughout this lifecycle, insiders have access to their organisation’s information. If organisations are going to protect their data better and reduce the frequency and impact of incidents, security controls must take account of the insider threat.
Information risk assessments will determine the appropriate controls for the specific threat events associated with each stage of the lifecycle that take advantage of the trust vested in insiders. As a minimum, basic cyber hygiene measures are vital. These include access control, segregation of networks, anti-malware solutions and patch implementation.
